Abstract
Six out of 25 species of primates most endangered are in Indonesia. Six of these primates are namely Orangutan, Lutung, Bekantan, Tarsius tumpara, Kukang, and Simakobu. Three of the six primates live mostly on the island of Borneo. One form of preservation of primate treasures found in Kalimantan is by conducting studies on primate identification. In this study, an android app was developed using the CNN method to identify primate species in Kalimantan wetlands. CNN is used to extract spatial features from primate images to be very efficient for image identification problems. The data set used in this study is ImageNets, while the model used is MobileNets. The application was tested using two scenarios, namely using photos and video recordings. Photos were taken directly, then reduced to a resolution of 256 x 256. Then, videos were taken in approximately 10 to 30 seconds with two megapixel camera resolution. The results obtained was an average accuracy of 93.6% when using photos and 79% when using video recordings. After calculating the accuracy, the usability test using SUS was performed. Based on the SUS results, it is known that the application developed is feasible to use.
[https://jurnal.ugm.ac.id/ijccs/article/view/65640]
Tags: CNN, Image Recognition, Mobile-based
Acara daring FMIPA on Research: Kiat-kiat menulis buku Best Seller - rekaman nya bisa disaksikan di bawah ini, silahkan, semoga bermanfaat.
[https://www.youtube.com/watch?v=cEgI6SBrxwM]
Tags: best-seller, buku
Webinar Internet of Things (IoT) dan Data Analytics (info) diselenggarakan oleh AKAKOM yang sekarang berubah menjadi Universitas Teknologi Digital Indonesia (UTDI) diselenggarakan pada 28 Oktober 2021 - bertepatan dengan Hari Sumpah Pemuda.
Dalam kesempatan itu, saya memberikan penjelasan terkait dengan konsep IoT, Piranti dan Konektivitas IoT serta Analisis data IoT, bagaimana penjelasan-nya? silahkan klik tautan Youtube nya, terima kasih dan semoga bermanfaat.
Webinar IoT dan Data Analytics
– silahkan klik tautan di atas untuk menyaksikan video-nya ==
Tags: akakom, data analytics, internet of things, iot, utdi
sWebinar yang diselenggarakan pada Jumat, 1 Oktober 2021 oleh Bisa.ai menjelaskan secara singkat terkait dengan penggunaan Kecerdasan Artifisial pda pengolahan data seismik.
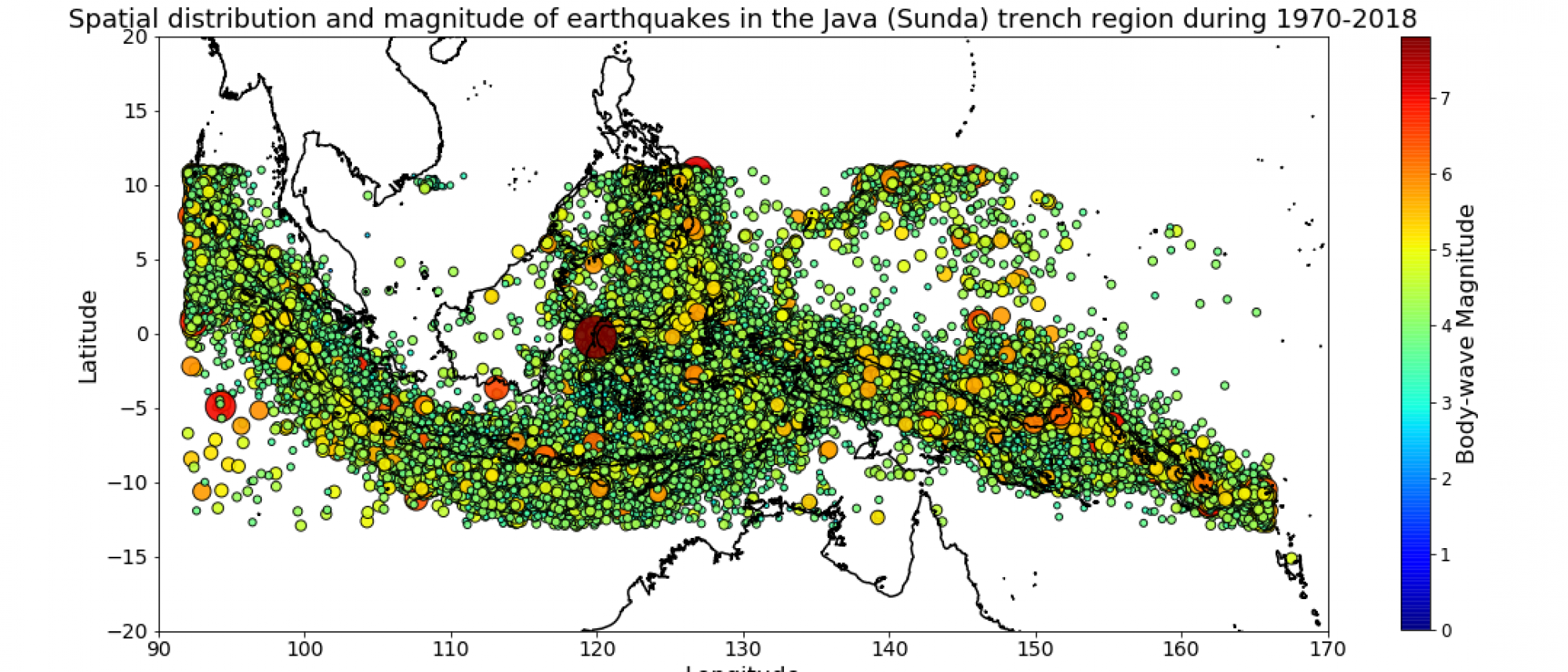
Mengawali webinar saya menampiokan distribusi spasial sebaran gempabumi di Indonesia, jangan kaget, jangan panik (perhatikan gambar berikut)
Selanjutnya saya berbicara tentang apa itu Kecerdasan Artifisial, kaitannya dengan Machine Learning dan Deep Learning. Bberapa penjelasan singkat terkait dengan aplikasi Machine Learning pada pengolahan data-data seismik, baik gempa bumi maupun vulkanik, dalam beberapa paper terkait. Selengkapnya silahkan menyaksikan VIDEO-nya (klik aja video-nya).
Semoga bermanfaat dan terima kasih.
Tags: deep learning, gampa bumi, kecerdasan artifisial, machine learning, seismik, seismologi
WORKSHOP - Riset dan Implementasi di Bidang Speech, Signal dan Music Processing - Sabtu, 8 Mei 2021
Implementasi Sinyal dan Speech Processing - Dr. Agfianto Eko Putro, M. Si.
== silahkan klik tautan di atas untuk menyaksikan video-nya ==
Tags: iaie, signal processing, speech
Sosialisasi Pembentukan Pengurus dan Anggota Asosiasi Kecerdasan Buatan DAY 2 - Minggu, 25 april 2021.
Pada kesempatan ini saya coba menjelaskan dengan singkat konten stranas Kecerdasan Artifisial di Indonesia, khususnya terkait dengan arah aktivitas atau penelitian Kecerdasan Artifisial di Indonesia. Silahkan untuk lebih jelasnya menyaksikan tayangan berikut…
Arah Aktivitas/Penelitian Kecerdasan Artifisial Indonesia
== klik tautan diatas untuk menyaksikan video-nya ==
Tags: ai, artificial intelligence, kecerdasan artifisial, stranas
Most of the communication protocols in the Industrial Control System (ICS) are vulnerable to cyber-attacks. Initially, the network protocol was designed for reliable performance, and thus did not incorporate data transmission security features. Therefore, ICS requires adequate data transmission security. This paper suggests improving the security of data transmission through a dynamic symmetric four-key-generators system, wherein the system anticipates cyberattacks by generating four keys before encryption. It involves four generators: a random initial key generator, a keystream generator, a key scheduling algorithm generator, and a pseudo-random number algorithm generator. In the receiver section, the system generates three keys before decryption to ensure data confidentiality and to avoid cyberattacks. The test results show that the proposed system key space is ≈22048 bits, meaning that the key is more secure from brute force attacks. As a result, the cipher data have a correlation value of 0.00007. The entropy value is 7.99, indicating that the cipher data is more secure. Also, speed tests show that the processing time still qualifies as real-time.
Program Studi Teknik Elektro, Universitas Muria Kudus mengadakan acara Kuliah Tamu 2020 dengan topik FPGA dan aplikasinya. Nara sumber: Dr. Agfianto Eko Putra, M.Si. (Program Studi S1 Elektronika dan Instrumentasi, Departemen Ilmu Komputer dan Elektronika, Fak. MIPA, Universitas Gadjah Mada, Yogyakarta)
Selamat menonton dan semoga bermanfaat, Terima kasih.
Kuliah Tamu 2020 - FPGA dan Aplikasi-nya
== silahkan klik tautan di atas untuk menyaksikan video-nya ==
Tags: FPGA, internet of things, iot, lecture, Mikrokontroler
Control system is widely used to monitor and control various industrial processes, such as oil and gas, smart grids, nuclear power plants, water treatment, telecommunication, chemicals, etc. Industrial Control Systems (ICS) require a secure communication network and real-time processing. However, most network protocols are designed only for reliable performance and are not equipped with adequate security systems. This study proposes to increase the security of data transmission but still pay attention to the speed test analysis to fulfill the real-time process. We introduce the BRC4 super encryption method with a combination of Beaufort and RC4 ciphers to improve data security, but still comply with real-time processing. The test results show that the proposed random initial key with at least 16 characters key length has a key space of (2) 128 bits. That means the proposed system is secure from brute forces attacks. The correlation and entropy analysis results for the largest data (IL-3) were 0.0001 and 7.99. Both show that cipher data’s security increases because cipher and plain data are very different and have very high randomness. The speed test results with the longest total time (encryption and decryption) and various key length combinations for IL-1, IL-2, and IL-3 data were 0.0303 seconds, 0.1555 seconds, and 0.7372 seconds, respectively. These results indicate that the proposed system still fulfills the real-time processing.
https://doi.org/10.1109/ISRITI51436.2020.9315339
Tags: Ciphers, Data models, Encryption, Integrated circuits, Protocols, Real-time systems, Security
Rekaman live Sabtu, 4 Juli 2020
Pada Roundtable ini akan membahas mengenai Digital Signal Processing dan Deep Learning dengan narasumber:
- Dr. Agfianto Eko Putra (Dosen DIKE, Fak. MIPA, Universitas Gadjah Mada, Ketua Aptikom Daerah Istimewa Yogyakarta) — Pembahasan: digital signal processing untuk kasus speech signal dan seismic dengan MATLAB;
- M. Octaviano Pratama, M.Kom (Chief Scientist BISA AI) — Pembahasan: klasifikasi low level dan high level speech feature dengan Deep Learning;
Tags: aptikom, bisa.ai, DSP, fft, filter, fir, iir, spektrum




Komentar Baru